PRIVACY AND INFORMATION SECURITY

Primax Group is committed to protecting customer information security to safe guard customer rights. The company has established management procedures for customer privacy and confidential information, adhering to the principle of "least privilege." Access to sensitive data related to customer projects is granted only after internal authorization, and the Group's information security department conducts regular reviews of security-related procedural documents to ensure timely updates that meet the required level of information security management in line with customer needs and demands.
Security Organization
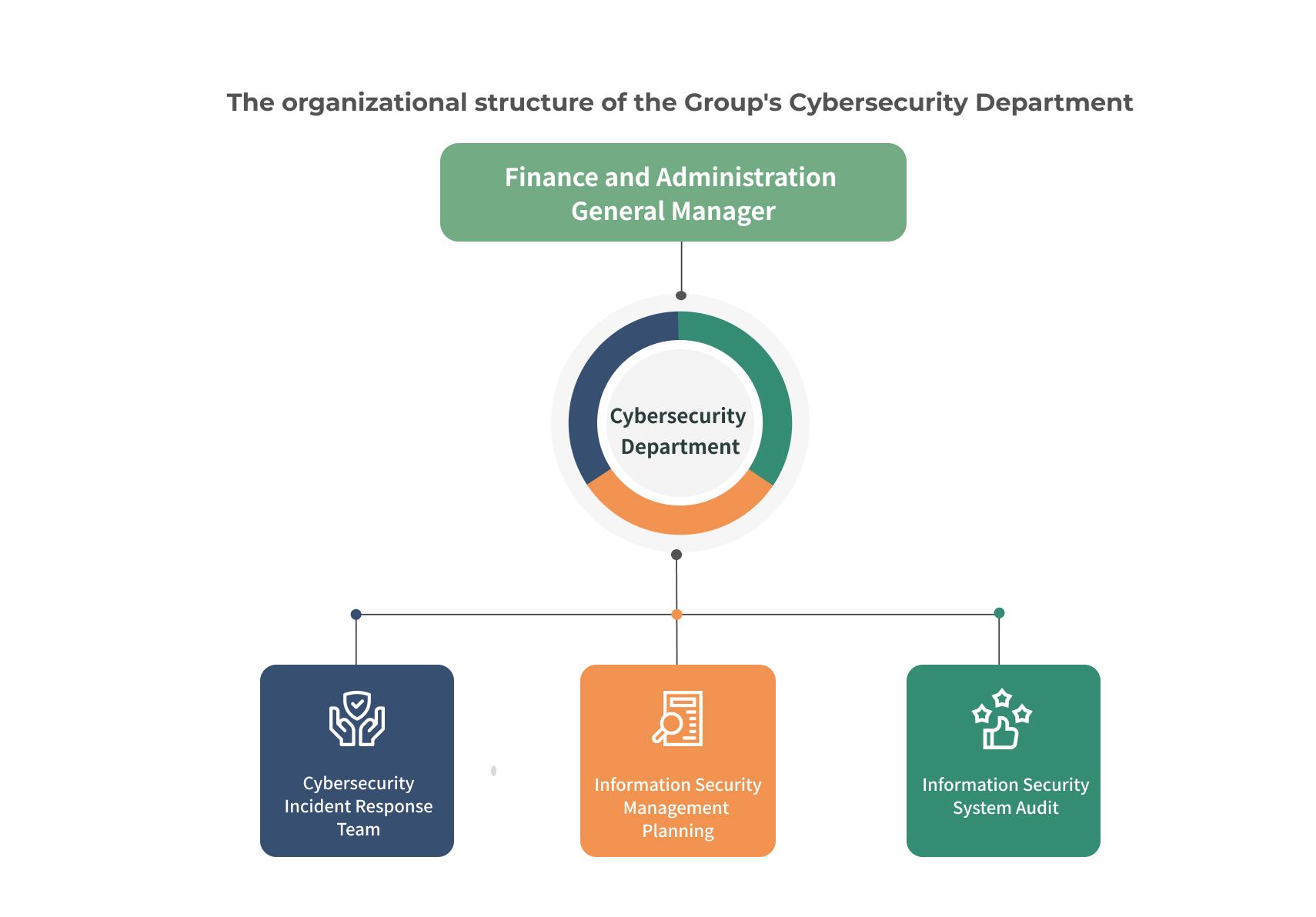
To improve the security management of the group, a Group Cybersecurity Department has been established, with the Chief Financial and Information Officer as the highest responsible person. The Information Security Department is responsible for driving information security policies and resource all ocation. It is staffed with dedicated cybersecurity professionals to ensure that all information security management standards and control measures are effectively and continuously implemented.
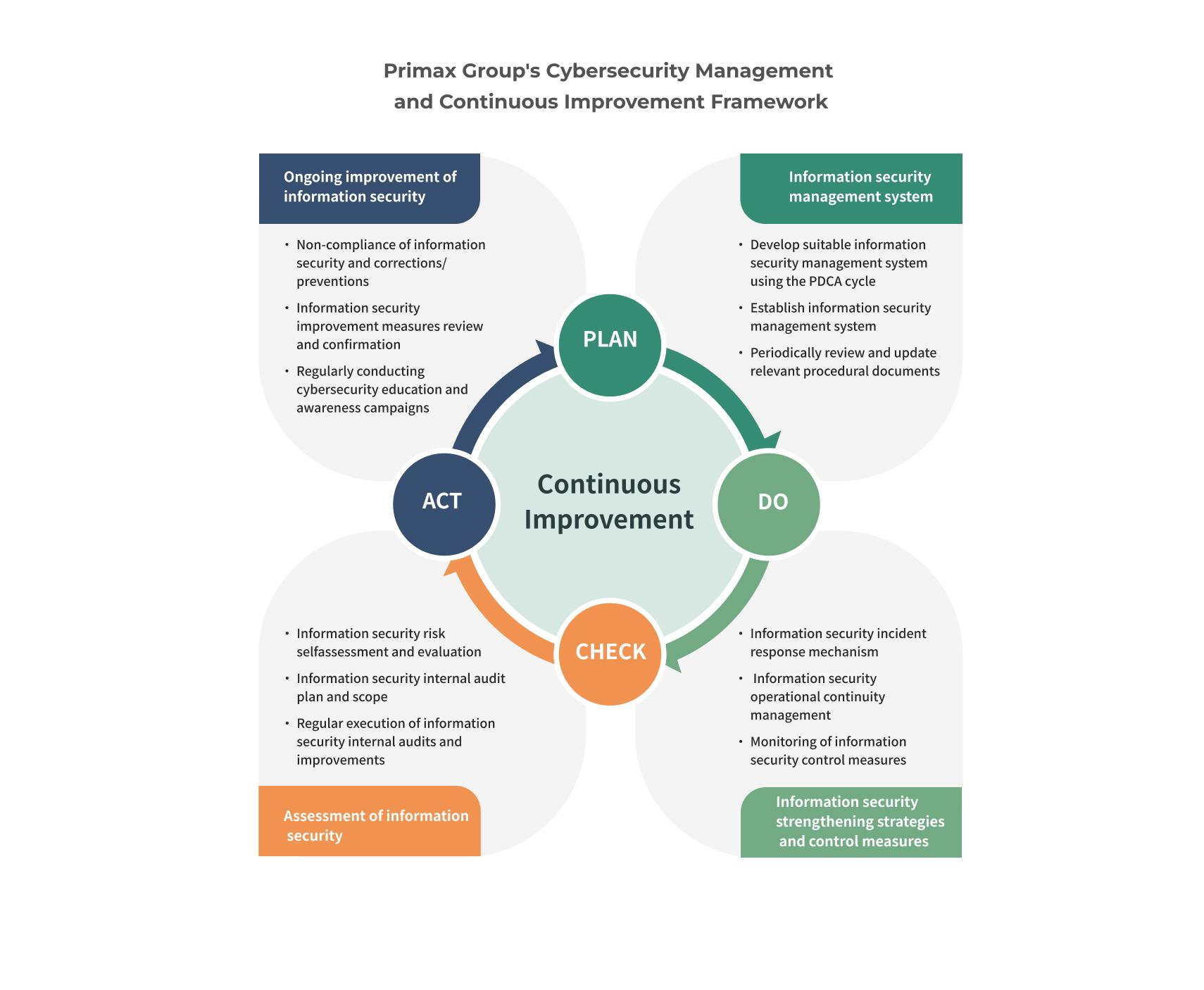
Primax Group's Cybersecurity Management and Continuous Improvement Framework
Cybersecurity Management Mechanism
All of customers' private and confidential information is disclosed on a need-to-know basis, and the Group has implemented three different types of control: People, Process and Technology to ensure the security of customers' private and confidential information. Below is a summary of the three controls:
- New hires are required to undergo Cyber Security awareness training, while all other employees are subject to regular re-training of information security. The purpose of this training is to enhance employees' awareness towards customers' private and confidential information.
- A corporate security organization has been assembled directly under the General Manager. It is responsible for incorporating people, processes and technology into safeguarding customers' private and confidential information at the highest level. This organization exists to ensure that the various activities and measures are implemented properly, and that customers' private and confidential information is protected at all times.
- All employees are required to sign a confidentiality agreement before commencing or terminating employment.
- Employees are prohibited from disclosing sensitive information to any internal or external party without the consent (or authorization) of the customer's project manager. Access to such information is granted only to the extent needed to serve the purpose.
- Customers' private and confidential information is protected before, during and after project until the product is discontinued.
- Network security equipment, software and anti-virus measures are constantly being enhanced to repel information security threats such as malware, botnet, virus, ransomware, and hack. Anti-virus and anti-hack platforms are being implemented throughout the Company.
- All systems and customer information are subject to access control. Only authorized personnel may access information for work-related purpose.
Cybersecurity Management Actions
To meet the requirements of internal information security regulations and external regulatory authorities, the group has established an Information Security Management System and information security management procedures. Nine information security objectives have been formulated, and the results of their achievement are recorded on a monthly basis.
01
Time of Abnormal Interruption of Dedicated Communication Line
02
Antivirus Software Virus Definition Update Achievement Rate
03
Network Equipment Failure Statistics
04
Statistics on Unauthorized Changes to Communication and Information Equipment
05
Incidents of Unauthorized Account Creation in AD / Mail Systems
06
Core Server Service Interruption Time
07
Failures in Backup of Critical Core Systems
08
Unpatched Critical Vulnerabilities Detected in System Scans
09
Statistics on the Number of Information Security Incidents
Cybersecurity Risk Assessment
The Company inventory the information assets and update the record book of assets periodically. Every year, the risks related to the information assets are appraised, and the high risk items are controlled, to lower the chance of risks and their impacts, for the purpose of ensuring the Company’s long-term cybersecurity.
Cases
Strengthening Network Firewalls and Network Control
Adopting New Technologies to Strengthen Data Protection and Backup
Establishing Endpoint Antivirus Measures Depending on Computer Types
Enhancing the Detection of Phishing Emails
Regularly Performing Social Engineering Email Testing and Offering Employee IT Security Awareness Training

Internal Audit of Cybersecurity
The information audit task force of the Cybersecurity Department establishes the evaluation indicators based on the risks. The self-assessment and inspection of cybersecurity are conducted annually. The outcome of assessment and supporting documents are sent to the Audit Department for verification. The Audit Department implements the information cycle audit every six months. Cybersecurity is one of the required items for audit. All the outcomes of audit are brought to the Audit Committee and the BOD regularly, at least annually.
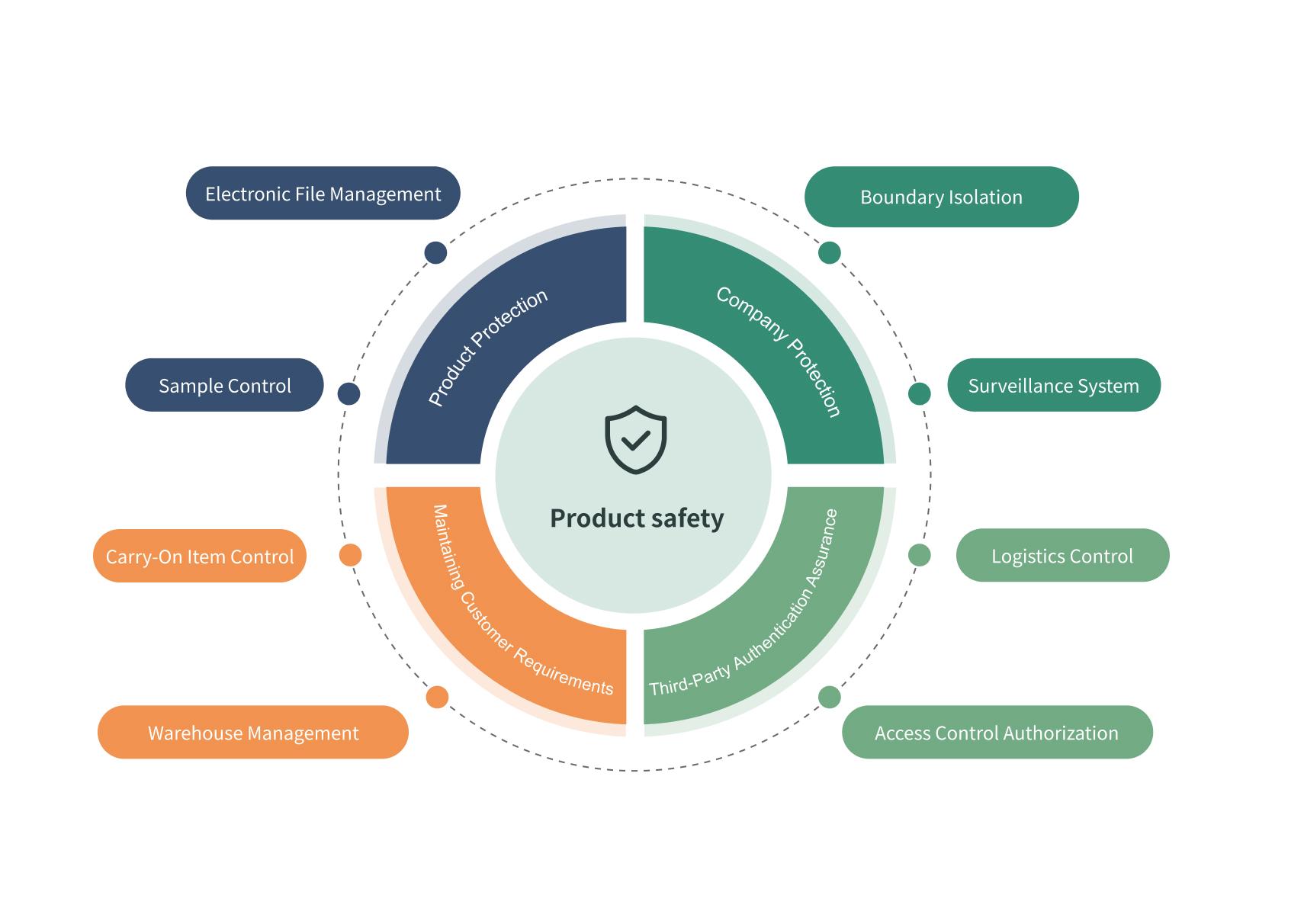
Product R&D and Manufacturing Safety
The research and manufacturing units of the company have consistently conducted research and manufacturing operations in accordance with the Group's information security policy and customer requirements and expectations. Through various physical and electronic control processes, the protection of product confidential information and process technology is ensured, while also maintaining compliance with customer requirements and relevant third party certifications.